sudo apt install libpam-google-authenticator
google-authenticator
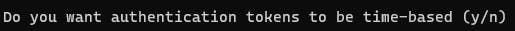
PAM (Pluggable Authentication Module) offers two types of tokens: sequential-based and time-based. Sequential-based tokens start at a certain point and increase after each use, while time-based tokens change after a set time. Google Authenticator uses time-based tokens. So choose y for yes.
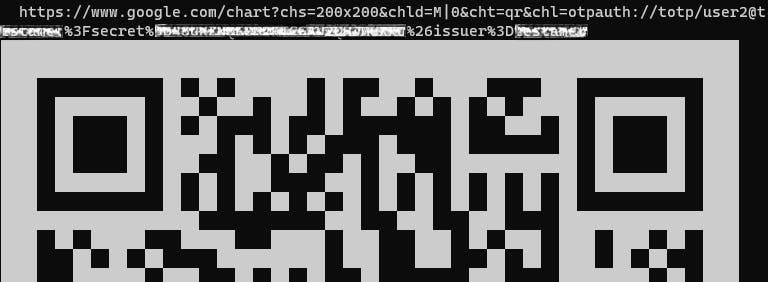
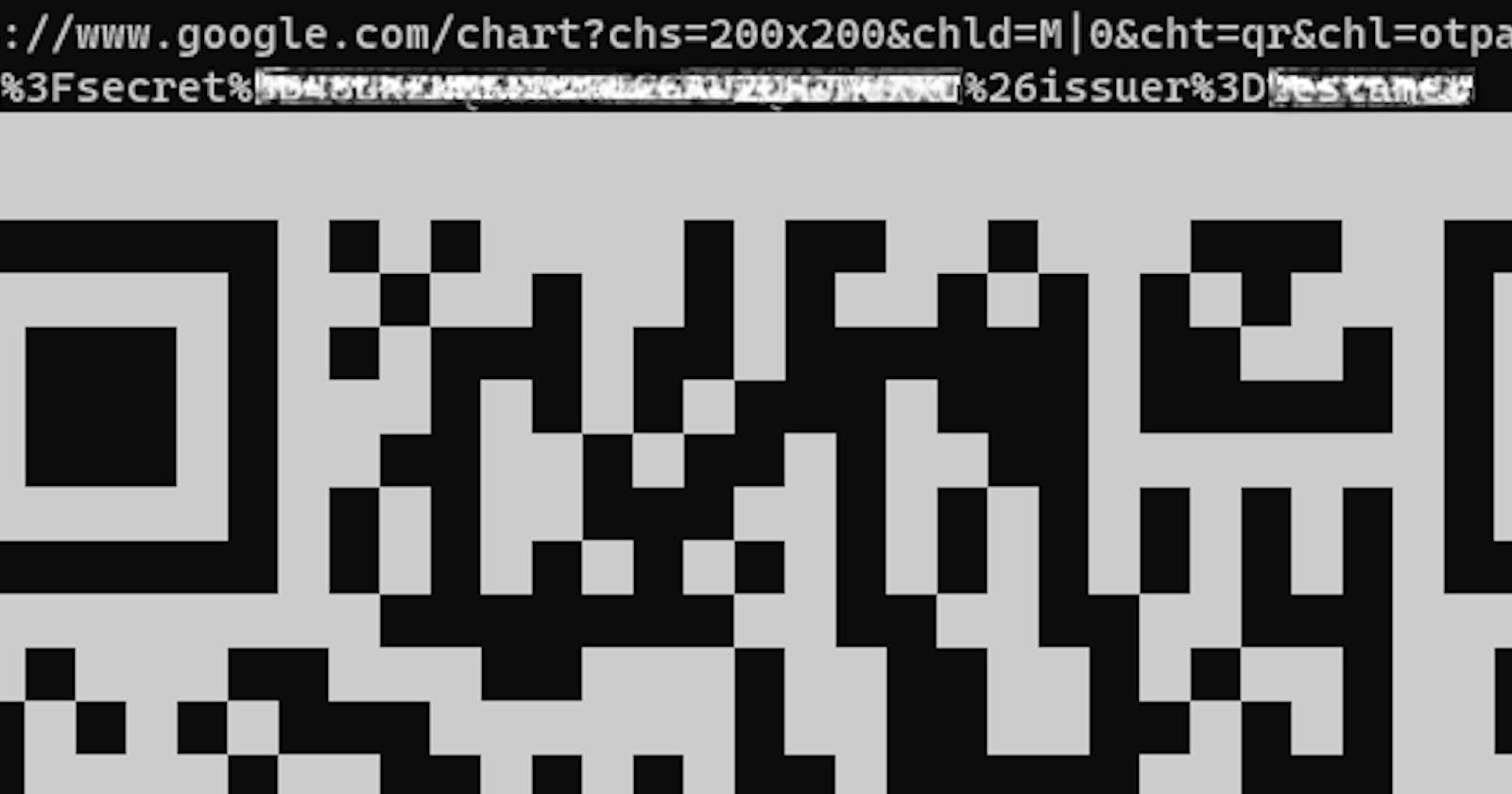
Then scan the QR given. If it's too big you can paste the URL above the QR but risking exposing your secret code in the browser.
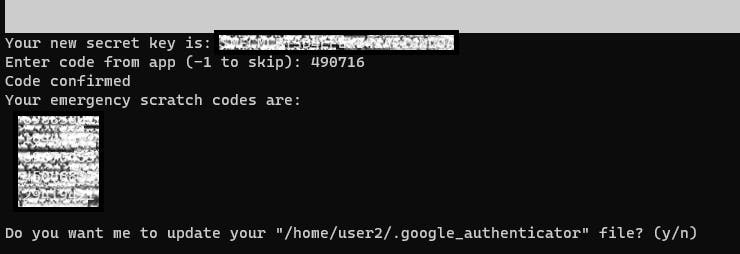
Copy your emergency codes in case your phone gets into trouble. If you forgot you can still view it in .google_authenticator file in the home directory. Choose y for the program to write the key and option.
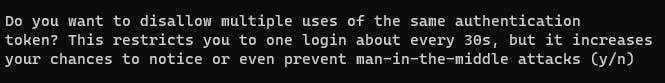
Selecting yes here is essential to prevent replay attacks. When you answer yes, it ensures that each code becomes invalid immediately after you use it. This security measure stops an attacker from intercepting a code you've just used and using it to log in as you. An example of a log if you choose yes is below.
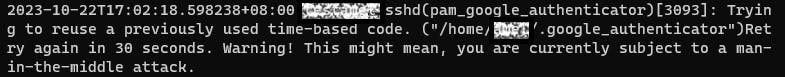

Selecting yes allows for up to 17 valid codes within a moving four-minute window. If you choose no, it limits this to 3 valid codes in a 1:30-minute rolling window. Unless you identify problems with the 1:30 minute window, opting for no is the more secure option. You can modify this setting later in the .google_authenticator file located in your home directory.
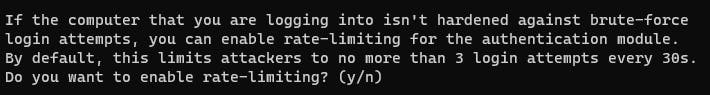
Rate limiting restricts the number of login attempts a remote attacker can make. It forces them to wait for some time before they can try again after reaching the limit. If you haven't set up rate limiting in SSH before, doing it now is a strong security practice that enhances protection against unauthorized login attempts.
sudo nano /etc/pam.d/common-auth
Add auth required pam_google_authenticator.so as the first parameter.
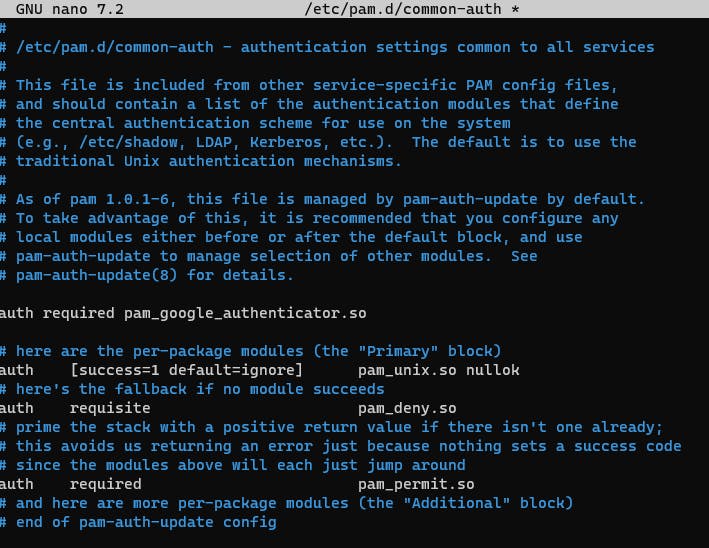
sudo nano /etc/ssh/sshd_config
Change KbdInteractiveAuthentication to KbdInteractiveAuthentication yes.

Then reload the secure shell.
sudo systemctl reload ssh
If you want to add a new user to your system make sure to add nullok in the end of auth required pam_google_authenticator.so.
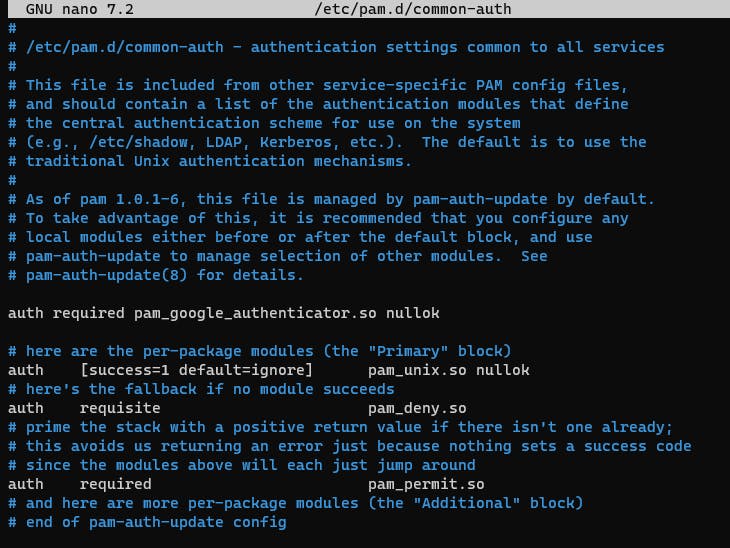
By doing this you can ask the new user to create their google_authenticator code.
After all users have their codes just remove the nullok to force MFA to all users.
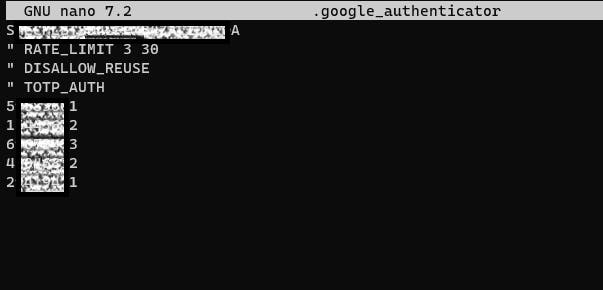
Here are some modifications you can make to this file:
To switch from time-based codes to sequential codes, change the line "TOTP_AUTH" to "HOTP_COUNTER 1."
If you want to allow multiple uses of a single code, remove the line "DISALLOW_REUSE."
To extend the code expiration window to 4 minutes, add the line "WINDOW_SIZE 17."
If you wish to disable rate-limiting for multiple failed logins, remove the line "RATE_LIMIT 3 30."
To adjust the rate-limiting threshold, locate the line "RATE_LIMIT 3 30" and change the numbers. The original "3" signifies the number of attempts over a period, and "30" represents the time in seconds.
To deactivate the use of recovery codes, simply remove the five eight-digit codes at the bottom of the file.
If everything goes right you will get this login screen :